About Netdelta
Flagging port scan deltas should be easy right?
Flagging port scan deltas should be easy right? Just download ndiff and use that? Ndiff can work for a one-off differential scan where an accurate, longer term, consistent, scheduled scanning requirement with reliable results, is not required. The ndiff option doesn't work. Why?...false positives of course. False positives in differential port scanning render the whole exercise useless. They come in a number of forms:
- Most common is the host time out - scanner detects from one scan to another that a host is missing, it will flag a delta,
but the host is actually up. This is a false delta. Netdelta retries the host over a user-configurable interval.
- Service time out. Also common is the service time out, where from one scan to the next, a service becomes unavailable, even
if the host is available. Netdelta keeps a history of past scan results and calls out red, amber, green on the likelihood that
the service delta is a false positive, based on the scan history and any previous occasions where the same delta was flagged.
- Service discovery scan time out. Discovery scans are set to run by default with Netdelta.
This has the equivalent effect as with using the "-sV" option with nmap. Sometimes they time out, and nmap uses the port number alone to
deduce the application layer service e.g. a port 443 TCP was previously a "http" port from its banner (surprisingly common),
but then becomes "https" from nmap's guessed service name. Therein a false delta is reported. Netdelta deals with this by performing
another analysis filter pass on the port scan data.
- tcp_wrapped services. This can occur for a variety of reasons (IDS can cause this for example), but either way, it causes
a false delta to be raised. Netdelta allows the user to ignore these issues with an admin setting.
- Proxy time-out. Sometimes, with a reverse proxy in front of advertised services, a time-out in the connection can occur.
- Netdelta caters for various other factors that can lead to a false delta.
Netdelta ...
- Maintains scan history in a backend database and provides analytics.
- Provides a RESTful API for consumption of data around port scans and deltas - more info is available on request.
- A webhook is available for triggering a vulnerability scan in response to a delta being discovered.
- If there's an unexpected change, it could be the result of unauthorised activity: hacking, malware, unauthorised change, shadow IT, etc.
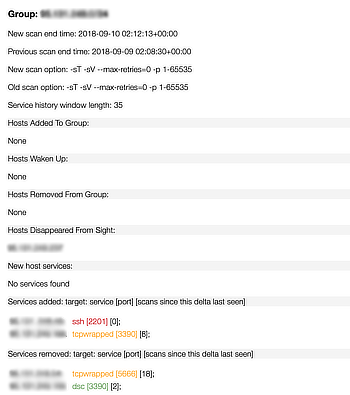
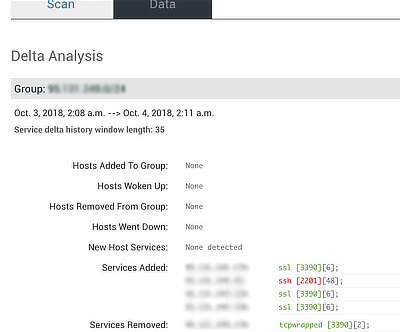
- Netdelta maintains a history of past scans and deltas and grades (red, amber, green) on the likelihood that the delta is a false positive.
- The changes alerted - host up, host down, new group member, new host appears (maybe a rogue host, unauthorised change, firewall misconfig), service(s) added, service(s) removed
- User-configurable email alerts.
- Schedule scans, or run instant scans against any configured group.
- User-configurable scan options.
 Netdelta
Netdelta